Native SAML 2.0 Support
The platform supports Single Sign On (SSO) via SAML2.0 with a third-party authentication authority. .
A pre-requeisite to setting up SSO is having a data integration so that the user accounts in ExpoPlatform and in the third party system are synchronised.
How SAML 2.0 Works
The general authentication flow is described in the diagram below:
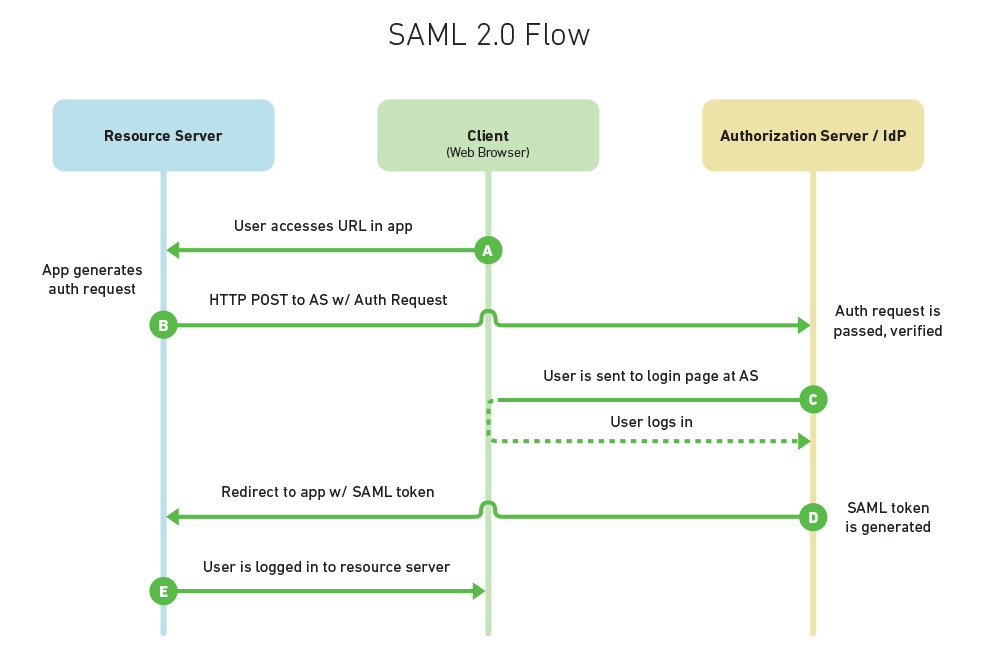
Service Provider (Resource Server) – this is the web-server you are trying to access information on, i.e. in our case this is a specific event on ExpoPlatform
Client – this the user is interacting with the Resource Server, like a web app being served through a web browser.
Identity Provider (Authorization Server) – this is the server that owns the user identities and credentials. It’s who the user actually authenticates with.
Here’s how the flow in the diagram above can be described:
A – a user opens their web-browser and goes to an event on ExpoPlatform, which no will not handle authentication itself.
B – to authenticate the user, the platform constructs a SAML Authnrequest, signs it and and encodes it, and redirects the user’s web browser to the Identidy Provider (IdP) in order to authenticate. The request contains the id of the event. The IdP receives the request, decodes it, decrypts it if necessary, and verifies the signature.
C – With a valid Authnrequest the IdP will present the user with a login form in which they can enter their username and password.
D– Once the user has logged in, the IdP generates a SAML token that includes identity information about the user which is their email. The Id takes the SAML token and redirects the user back to the Service Provider (i.e. ExpoPlatform).
E – ExpoPlatform verifies the SAML token, decrypts it, and extracts out identity information about the user. ExpoPlatform now logs the user into its system.
At the end of the process the user can interact with ExpoPlatform as a logged in user. The user’s credentials never passed through ExpoPlatform, only through the Identity Provider.
Parameters Setup
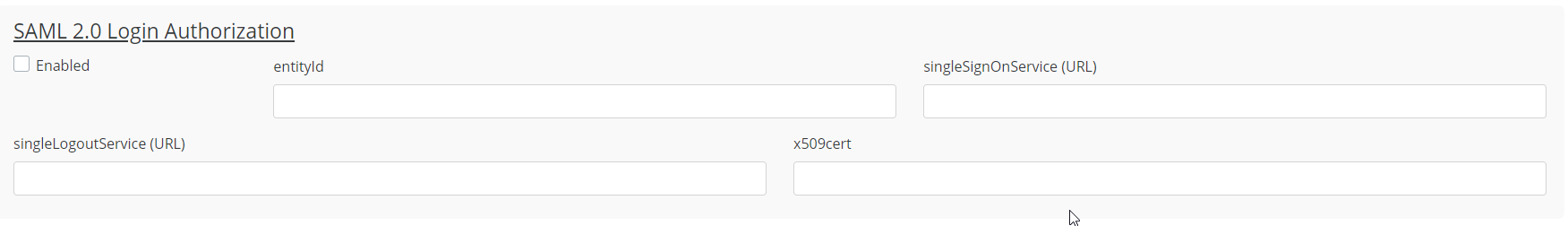
The following parameters are required for the integration:
entityID
singleSignOnServiceURL (URL)
singleLogoutService (URL)
x509cert
To configure this, go to Event Setup → Genera → Settings, and navigate to the SAML2.0 set-up section, and fill in the appropriate fields, then click “Enable” and click “Save” to apply changes.
Once this is set up, all users will need to authenticate through the IdP rather than via the platform, and all platform pages will be locked behind log in and require authentication. Users who are already registered for the event will be logged into their account when they log in via SSO. If a user is in the global database but is not registered on the particular event they are trying to access, they will be able to access the platform as a non-logged in user until they register. Once registered, they will be logged into their account.
